How to Unlock a RAR File Using Brute Force Attacks
Trying to access important data locked away in a RAR file but can't remember the password? You might have come across the term "bruteforce RAR file" in your quest for a solution. This article will delve into the intricacies of brute force attacks, their ethical implications, and some alternative methods for unlocking RAR files.
Understanding Brute Force Attacks
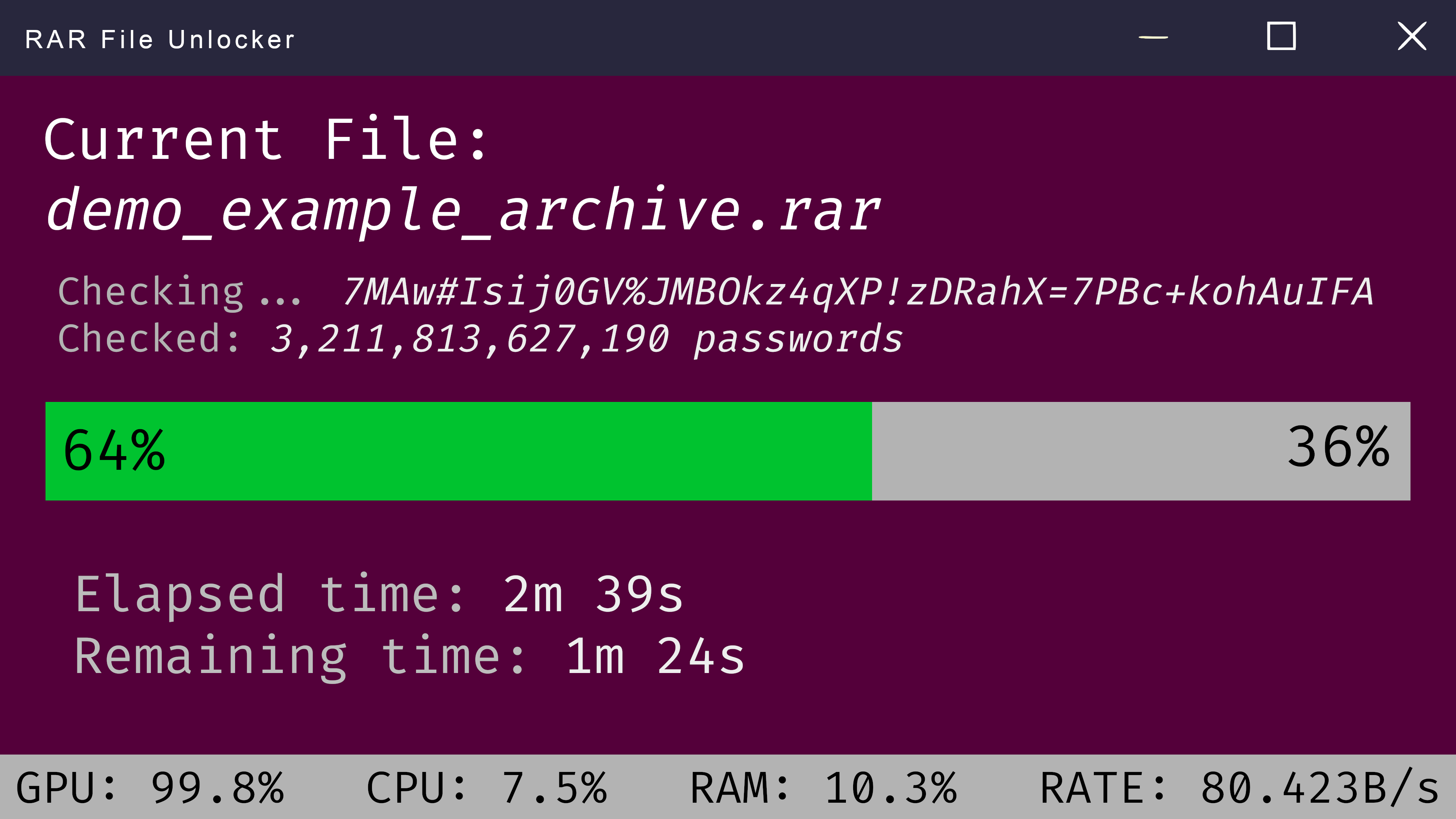
A brute force attack is a trial-and-error method used to gain unauthorized access to systems or encrypted files like RAR archives. It involves systematically trying every possible combination of characters until the correct password is found. While conceptually simple, brute forcing can be incredibly time-consuming, especially for complex passwords.
Brute Forcing RAR Files: Factors to Consider
The success and duration of a bruteforce RAR file attack depend on several factors:
- Password Complexity: Longer passwords with a mix of uppercase and lowercase letters, numbers, and symbols are exponentially harder to unlock than simple ones.
- Processing Power: A powerful computer with a fast processor and sufficient RAM can significantly speed up the brute force process.
- Software Tools: Several software tools are specifically designed for bruteforcing RAR files. These tools often leverage the power of your computer's GPU for faster password unlocking.
Ethical Considerations
It's crucial to remember that using brute force techniques to access data that doesn't belong to you is illegal and unethical. Before attempting to bruteforce RAR files, ensure you have the legal right to access the data within.
Alternatives to Brute Force Attacks
While brute force can be an option for recovering forgotten passwords, several alternatives exist:
- Password Recovery Software: Specialized software utilizes more sophisticated techniques like dictionary attacks and mask attacks, which are often faster than brute force.
- Password Hints: If you've set up password hints for your RAR archives, try recalling them as they can provide valuable clues.
- Contacting the File Owner: If you received the RAR file from someone else, reach out to them to request the password.
Protecting Your RAR Files from Brute Force Attacks
Here are some tips for securing your RAR files:
- Strong Passwords: Use long and complex passwords with a combination of uppercase and lowercase letters, numbers, and symbols.
- Password Managers: Employ a reputable password manager to generate and store your passwords securely.
- Multi-Factor Authentication (MFA): Whenever possible, enable MFA for accounts that manage or store your RAR files.
Conclusion
While the term "bruteforce RAR file" might seem like a quick solution for accessing locked archives, it's essential to understand the ethical implications and potential legal ramifications. Exploring alternative password recovery methods or focusing on preventative measures like strong passwords and MFA is always recommended. Remember, responsible data security practices involve ethical considerations and respect for data ownership.
Learn how to protect yourself from brute force attacks and secure your valuable data.
 Windows
Windows MacOS
MacOS Linux
Linux